Can VPNs Bypass Firewalls?
Firewalls are key for keeping your online data safe and private. They protect against cyber threats. But, they can also be a hassle.
Many of us have hit a roadblock at school or work because of firewalls. You might try to open your favorite social media or search for something, only to get an error. This is what happens when a firewall blocks you.
Don’t worry, we’ve got you covered. We’ll show you how to use a VPN to dodge annoying firewalls. This way, you can access the internet freely. We’ll also discuss other options and alternatives to get past a firewall.
Can You Use a VPN to Bypass Your Firewall?
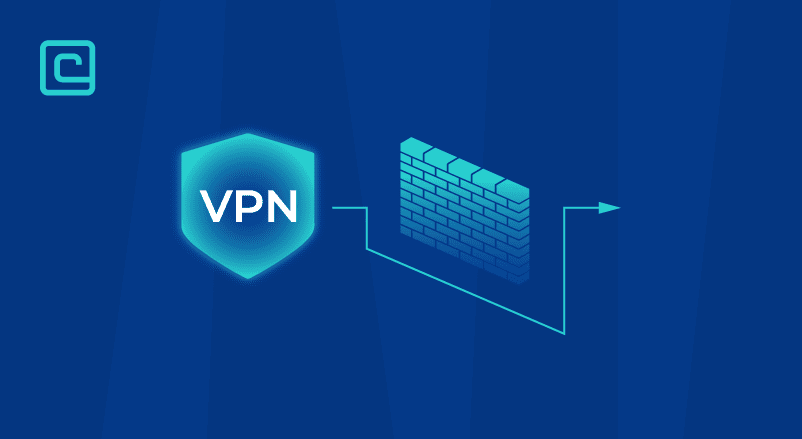
Yes, you can use a VPN to get past your firewall. Think of a VPN as a tunnel through the firewall. It uses a protocol to hide your data, making it hard for the firewall to detect.
How does a VPN tunnel work? It’s like a private network inside a bigger one. Most VPNs use protocols like OpenVPN and WireGuard to create this tunnel.
When you connect to a VPN, your IP changes to the VPN’s. This makes it seem like you’re somewhere else. All your traffic is also hidden in the VPN’s tunnel.
But, does a VPN hide your search history? Sadly, no. Your browser stores history locally, so a VPN can’t hide it.
Even though a VPN hides your traffic, it can’t control all apps. To browse privately, use Incognito mode or a privacy-focused browser.
Test Your VPN Knowledge – Take A Quiz!
How Do Firewalls Work?
A firewall is a system that controls network traffic. It acts as a barrier between your network and others.
For example, schools might block social media to keep students focused. Streaming sites also use firewalls to block viewers from certain areas.
Some governments have nationwide firewalls to control what people can see online. The Great Firewall of China is a well-known example.
Why Use a VPN to Bypass Your Firewall?
Using a VPN is better than other methods for several reasons. These include effectiveness, ease of use, privacy, and security. Let’s explore each reason in more detail.
VPNs are very effective because they cover your entire network. With one click, you can access any site. You can also choose from many servers and customize features.
Using a VPN is also the most convenient way to bypass firewalls. It’s easy to use and doesn’t require technical knowledge. If you’re more tech-savvy, you can customize it further.
The biggest advantage of using a VPN is the extra privacy and security it offers. Other methods might work, but they can’t match the protection a VPN provides.
Looking to browse privately at work or get free Internet in censored areas? A VPN keeps your privacy safe. It encrypts your data, making it unreadable to anyone who tries to intercept it.
How to Bypass a Firewall Using a VPN
Now, let’s talk about using a VPN to hide your Internet traffic. It’s quite simple. Here’s how to bypass a firewall with a VPN:
- Subscribe With a VPN of Your Choice
- Download the App
- Connect to the Server
- Bypass the Firewall!
After a few seconds, you’ll be connected to your chosen server. Then, you can browse the Internet freely, without any firewall blocks.
How Do I Get Around a Firewall Other Than With a VPN?
Using a VPN is the best way to get around a firewall. But, there are other options too. If you don’t want to pay for a VPN or can’t use one where you are, here are some alternatives:
- Use a Proxy – this method is similar to using a VPN to bypass firewalls, mainly in the sense that you’re using additional software that acts as an intermediary and tricks the firewall.
- Use Your Phone as a Hotspot – one creative way to get around a firewall is to utilize your phone. If your carrier supports tethering, you can share your mobile device’s data and use your phone as a hotspot. This is a simple, efficient, and hassle-free way to bypass any firewall.
- Use Google Translate – another inventive way to go around a firewall is to employ Google Translate. This nifty tool loads the contents of the page on the server, translates it, and sends the result to you. It practically does the same task as a proxy server.
- Use Ultrasurf – Ultrasurf is a freeway product dedicated to circumventing Internet censorship that’s been around for two decades. It employs encryption protocols for privacy and uses an HTTP server to bypass firewalls and Internet censorship in general.
FAQs
Which VPN can bypass any firewall?
There are a few top-notch VPNs that can get past any firewall. NordVPN, Surfshark, and ExpressVPN are some of the best for this purpose.
Do firewalls work with VPNs?
Yes, you can use a firewall while using a VPN at the same time. In fact, organizations and environments that require complex and impenetrable networks generally deploy these two simultaneously. A VPN encrypts your information and protects your privacy, while the firewall blocks any undesirable traffic.
How do hackers get past firewalls?
Cybercriminals can get past firewalls in several different ways. For example, they can exploit a DNS leak or employ an encrypted injection attack. Often, hackers get past a firewall by exploiting the user as the network’s weakest link. They do so through social engineering or manipulating people into doing things.
Considering this, a VPN can help you stay safe from malicious hackers who are out for your data. As it hides your IP and encrypts your traffic, it serves as a superb hacking deterrent. So, if you want to protect your device from hackers, using a VPN is a great way to go about it.
Conclusion
Running into a firewall might be discouraging and annoying, but in reality, it shouldn’t present any significant problem. With sufficient knowledge, you won’t have any trouble bypassing firewalls on any network, whether it’s at school, work, or any other environment.
And, as we’ve discussed in great detail above, a VPN does go through a firewall without much issue and is the option to go with. With a VPN service, you get both performance and protection. Of course, for this to be true, you should pick a solid VPN that can reliably go around firewalls whenever you need it to.
Lastly, if you want to explore alternative methods, the tools we’ve outlined above can be very useful for bypassing firewalls. All that’s left now is to pick the tool for the job and make firewall blocks a thing of the past!
Cybersecurity and VPN researcher

