What is VPN Tunneling? – Definition, Significance, and Types

Understanding the concept of tunneling is key to knowing how a VPN works. As the name suggests, a VPN tunnel is a secure link between your device and the internet. While browsing the internet, a VPN routes your connection through a private, secure tunnel so that your IP is hidden and your data is encrypted.
A VPN tunnel is no different from a real-life tunnel that you see while traveling in a train. Once you’re in the tunnel, it protects you from elements such as rain, sunlight, and landslides. In the online security world, the bad elements are snoopers, hackers, and entities such as your ISP and the government.
Need a better definition? Check out our detailed explanation of VPN tunnels.
What is a VPN Tunnel?
A VPN tunnel is a virtual link between your device and the internet which hides your IP address and encrypts your traffic. Virtual VPN tunnels use advanced protocols and AES-256-bit key encryption. Your data is hidden and protected from hackers inside a VPN tunnel.
A VPN tunnel can only be activated via a VPN client such as those offered by NordVPN and Atlas VPN. The difference lies here: a VPN tunnel is created by a VPN and is influenced by the protocol governing it.
In other words, a VPN tunnel is responsible for two things:
- Encrypt your web traffic (to hide your data)
- Route your encrypted connection via a VPN server (to hide your IP)
Note: Just installing a VPN isn’t enough to be protected online. You have to switch it on to activate the tunnel.
It is one of the main reasons why you should choose a VPN that uses advanced protocols like OpenVPN and WireGuard. They have the most advanced encryption. No wonder the US military uses them.
Test Your VPN Knowledge – Take A Quiz!
How Does a VPN Tunnel Work?
Assume that you have installed a VPN on your Android smartphone. The moment you turn it on, all your web communication – such as browsing, video streaming, and instant chatting – will be routed through a VPN server. You can choose this server and its location according to your needs.
At this point when the VPN is switched on, the link between your phone and the chosen server becomes encrypted. Your web communication is first encrypted by the VPN software and then routed through the server. The combination of this encryption and routing is what creates a tunnel as described in the picture below.
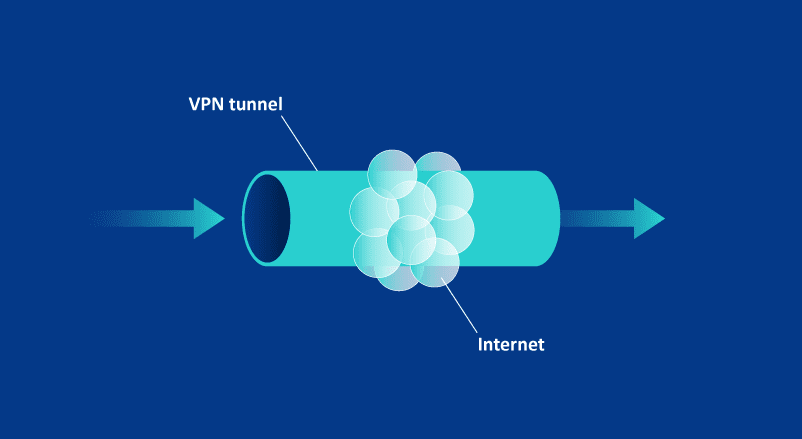
As you can see, the tunnel is a virtual, private network within the larger network i.e., the internet. And if you missed it, that’s the full form of VPN. If you think about it, tunneling is the core action in a VPN.
This tunneling action has several benefits. For starters, it hides your data through encryption. No one can know what websites you’re visiting and what content you’re consuming. If a hacker attempts to intercept your connection, all they will see is garbled text. This is the 256-bit key encryption doing its job. It can only be cracked open using a unique cryptographic key.
In addition to encryption, the routing action also conceals your online identity. Your IP address (or web location) is cloaked by an arbitrary address generated by a VPN server, which separates you from all your actions. As a result, a VPN tunnel effectively hides your tracks online and protects you from hackers.
As I have explained above, this dual action of VPNs is what makes them a superb privacy tool.
That also brings up the question: are VPN tunnels really unbreakable?
How Secure is VPN Tunneling?
VPN tunneling is dependent on the base protocol adopted by the VPN provider. The security of the tunnel is influenced by this protocol, which mainly dictates the encryption method.
For instance, OpenVPN is an open-source VPN protocol used by military organizations and businesses. The feature of this protocol is that it uses AES-256-bit key encryption and 2048-bit RSA authentication to encrypt data. As of 2022, these are the most advanced technologies used in data protection.
They prevent data breaches because while encrypting data is easy, decrypting is whole another ball game. RSA-based asymmetric encryption (used by OpenVPN and WireGuard) focuses on making decryption harder . Hackers and governments will have to implement brute-force attacks to break such encryption. This makes OpenVPN and WireGuard very, very difficult to crack.
Can a VPN Tunnel Be Hacked?
Unfortunately, yes. A VPN tunnel can be hacked but it’ll take incredible computational power and lots of computations and permutations for someone to do so. As of 2022, VPN tunnels that use asymmetric encryption have never been reported to be breached. At least such reports are not in the public domain.
However, we believe that government intelligence agencies have made some leaps in this regard. The good thing with that is that it’ll lead to the invention of new, stronger VPN tunneling technologies.
The bottom line is that VPN tunnels that use advanced, military-grade encryption are incredibly secure. Those that use older encryption methods – like PPTP and IKEv2 – or no encryption at all are vulnerable.
As general users with regular web interests, you and I are pretty much protected from such advanced brute-force attacks. Hackers and governments usually have high-profile targets. We should ideally be focusing on hiding our online tracks. The key is to continue using VPN across all devices where we access the internet.
Why Choose a VPN with a No-Logs Policy?
A lot of VPN users wonder if the threat of privacy intrusion is from the world wide web or their VPN company itself. Do they need to worry about the tunneling protocol if the VPN itself logs their activities?
Well, that’s why I recommend going only for reputable VPNs out there. The best way to surf the web today is to use a VPN service that has a strict no-logs policy. Like NordVPN, Surfshark, or Atlas VPN.
Types of VPN Tunneling Protocols
That brings us to the types of VPN tunnels available. These differ by the encryption technology, speed, implementation ease, and other security features. Here’s a quick look at the most common VPN protocols.
OpenVPN
It’s an open-source tunneling protocol considered the best in the online security world right now. It’s known for:
- High-speed tunneling
- AES-256-bit encryption
- Compatibility with all operating systems including Solaris and OpenBSD
WireGuard
The second-best tunneling protocol out there, WireGuard is relatively new and less complex than OpenVPN. It’s preferred for the following reasons:
- High-speed tunneling
- Uses ChaCha20 encryption algorithm
- Uses fewer resources than other protocols
- Open-source and lightweight
L2TP/IPSec
Layer 2 Tunnel Protocol is usually tied with Internet Protocol Security (IPSec) for VPN applications. It offers slower speeds but is still preferred because it:
- Provides strong authentication and encryption
- Has no known vulnerabilities
- Is easier to develop on
IKEv2/IPSec
It’s a combination of security protocol IPSec and tunneling protocol Internet Key Exchange version 2 (IKEv2). Its salient features are:
- Easy switching/reconnection
- Uses fewer resources
- High-speed tunneling on mobile devices
SSTP
Secure Socket Tunneling Protocol is preferred by VPN providers as it has native Microsoft (Windows) support. That makes it easier for companies to provide tunneling and firewall services. Other highlights include:
- Uses 256-bit SSL keys for encryption
- Compatible with some operating systems (through third parties)
- Easy setup
- Doesn’t use fixed ports
PPTP
Point-to-Point Tunneling Protocol is the oldest of the lot and is not preferred due to poor security features. In retrospect (the late 1990s), it was very useful because:
- Works with dial-up connections
- High-speed connectivity
- Easy setup
Which VPN Protocol Should You Use?
Most VPNs have a function where you can switch between available protocols. As I’ve noted before, it’s best to stick to OpenVPN or WireGuard. The second-best option is L2TP/IPSec.
In case you need better speed, I recommend switching servers before considering a protocol change. Even then, it’s better to upgrade to a high-speed plan than compromise by using a less-secure tunneling protocol.
A Note on Split Tunneling
Split tunneling is a nifty little VPN feature that allows you to route specific applications outside the VPN.
Say, you want to route all your web communication through your VPN software except Telegram messenger. Just add Telegram to the split tunneling settings (whitelist) of your VPN client. Telegram will communicate outside the VPN tunnel through your regular internet.
Split tunneling is useful when you want to free up some load off your VPN client. It can also boost speed if you have multiple web-based applications running simultaneously.
Please note that split tunneling will make your communication (on the specific applications) unsecured and vulnerable.
Final Thoughts on VPN Tunnels
VPN tunnels are the most integral part of how VPNs function. They are governed by protocols and are responsible for hiding your IP address and encrypting your data when you communicate over the internet.
Choosing the right VPN tunnel is crucial to ensure that you, your device, and your data are protected from cyber threats. OpenVPN and WireGuard offer the safest tunnels for most users.
Need more information to choose the best VPN tunnel? Check out our guide.

| 🌐 Website: | nordvpn.com |
| 🏢 Headquarters: | Panama |
| 📍Servers/Countries: | 5800+ servers in 68 countries |
| ₿ Accepts Cryptocurrency | Yes |
| 💸 Deals & Coupons | Get 68% OFF + 3 months FREE |
VPN and privacy researcher


